Eliminating Distraction with CTI
Cyber threat intelligence (CTI) can help organisations identify relevant threats, but what if its real superpower was the exact opposite?

Cyber threat intelligence (CTI) can help organisations identify relevant threats, but what if its real superpower was the exact opposite? At a time when there are plenty of headlines about the latest threats, knowing what not to focus on is increasingly valuable to security leaders.
CTI guidance often emphasises how an intelligence-led approach can help organisations focus on prominent threats in their sector and region. In this article, I flip this around to explore how CTI can remove noise.
Headlines Distort our Perspective
Rather than dashing from headline to headline, security functions are better off building a data-driven understanding of their threat landscape. That’s because interesting and newsworthy threats are often very different from the ones you need to care about.
Let’s rewind to March 2020, when the West was hunkering into lockdown. There was understandably huge concern around COVID-19 and its potential impact on our lives. Headlines on how the pandemic might impact the cyber threat landscape inevitably followed with reports claiming a 667% increase in COVID-themed phishing.
With a sharp uptick in pandemic lures, security leaders might have been tempted to allocate significant resources to tackling COVID phishing – perhaps through attention-grabbing awareness campaigns or heavy-handed email filtering. But, this would have been a mistake.
The threat of COVID phishing was significantly inflated. There may have been a sizeable increase in pandemic-themed social engineering, yet it started from an extremely low baseline. Focusing on the increase alone, therefore, created a distorted perspective.
A more objective and useful approach would be to ask instead what proportion of phishing emails featured references to the pandemic, or how successful they were compared to traditional lures. Here, the data told a very different story.
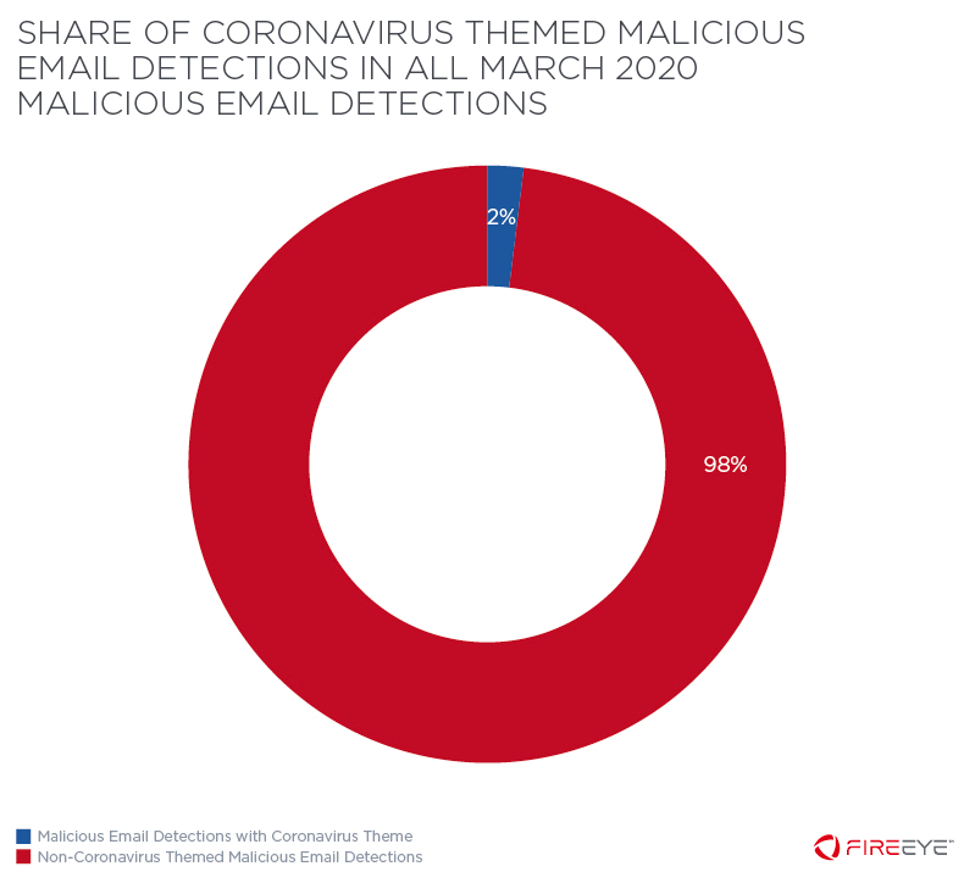
As a study by Mandiant at the time highlighted, only two per cent of malicious emails in March 2020 contained COVID-themed lures. The media furore was focused on a very narrow slither of all phishing activity.
Avoid Overcorrection
CTI can also provide a measured perspective on relevant threats that helps security functions stay grounded on what matters. The volume and breadth of different cyber threats make it all too easy for security leaders to lurch one from crisis to the next.
This is where CTI plays an essential role in zooming out from the threat of the day to provide a broader perspective. I have seen this play out all the time with Russia-Ukraine. It goes without saying that Russian cyber concerns are reasonable and valid, with organisations right to bolster their defences against prominent Russian attack techniques. Yet, one of the biggest dangers I have observed in the last year is a tendency for security functions to overcorrect and focus almost exclusively on Russian threat actors.
Mature CTI functions, on the other hand, recognise that Russia is just one of many relevant threats. By consulting a regularly updated threat profile that captures the breadth of relevant threats, they have maintained broader situational awareness beyond Russia. This might include increasingly aggressive Chinese cyber operations or the ongoing scourge of ransomware for instance. Here, CTI has helped organisations maintain a grounded perspective on what matters.
Another time where we frequently see overcorrection is around supposedly ‘critical’ vulnerabilities. These vulnerabilities attract a lot of attention due to a combination of media hysteria and a tunnel vision perspective that focuses almost exclusively on the negative impact of exploitation rather than whether it is being exploited.
The reality is that many of these critical-rated vulnerabilities are very difficult to exploit and are rarely targeted in practical settings. Vulnerability threat intelligence, therefore, also helps security functions to avoid overcorrection. By plugging in data on active threats – in this case, whether a vulnerability is being actively exploited – security functions can avoid hitting the panic button for vulnerabilities that don't pose a serious threat in practice.
Overcome Novelty bias
The security community tends to focus on what is new and interesting. This makes for fascinating conversations, yet is completely detrimental to securing networks.
Novel attack techniques are almost always only used by a very small handful of threat actors. Only hyper-mature security functions should be dedicating serious time to mitigating unusual attack techniques. For most, they represent a significant distraction.
Thee role of artificial intelligence (AI) in offensive cyber campaigns comes up a lot in public talks and panels. This is unsurprising as it is certainly an interesting topic. Yet, precisely because it's interesting, the threat posed by AI in cyber operations has inevitably been inflated.
There may be some isolated examples where AI has been used in cyber campaigns. It will no doubt become a more significant concern in the years ahead. However, for the majority of organisations still struggling to nail security fundamentals, AI shouldn’t be a focus area.
When done right, CTI should provide a far more grounded perspective that identifies what matters, rather than what is trending on social media. For example, Mandiant’s annual M-Trends report outlines the most frequently observed attacker techniques. These data-driven insights provide security functions with decisive quick wins as mitigating common attack techniques can dramatically reduce cyber risk.
Striking a Different Tone
The cyber security industry is already dealing with far more noise than it can handle. Security leaders crave focus in today’s climate. This means the ability to remove distractions is more helpful than ever. However, its value is chronically underestimated.
This provides huge opportunities for CTI providers to leverage their data to not only identify what matters to organisations, but to place renewed emphasis on helping security functions navigate distraction and sidestep cyber doom-mongers.
Identifying distraction points would make for a radical shift in messaging for an industry known to focus on the latest shiny threat actor. But, it would also strike a more grounded and accessible tone.
